Riverbed® NetProfiler oferă analize ale fluxului de rețea pe care le puteți utiliza pentru a diagnostica rapid problemele de rețea și pentru a identifica amenințările de securitate înainte ca utilizatorii finali să își dea seama că există o problemă.
Riverbed NetProfiler combină datele privind fluxul de rețea cu metrici de flux bazate pe pachete pentru a oferi monitorizare, analiză și raportare proactive. Folosiți NetProfiler pentru a răspunde la întrebări precum: cât de mult trafic am, cine îl folosește, încotro se îndreaptă și cum este prioritizat?
POSIBILITĂȚI
Organizațiile IT trebuie să înțeleagă modul în care performanța degradată afectează performanța rețelei și a aplicațiilor și, în cele din urmă, performanța afacerii. NetProfiler utilizează analiza comportamentală pentru o monitorizare proactivă. Acesta stabilește o bază de referință pentru performanța normală și alertează asupra schimbărilor imediat ce acestea apar – de obicei, înainte ca utilizatorii să conștientizeze că performanța se degradează.
NetProfiler automatizează cartografierea tranzacțiilor aplicațiilor cu infrastructura lor de bază, astfel încât definițiile și interdependențele aplicațiilor să fie exacte. Acest lucru vă ajută să creați hărți de servicii care accelerează identificarea problemelor în ecosistemele de aplicații complexe și să planificați inițiative de consolidare a centrelor de date, cloud, recuperare în caz de dezastru sau virtualizare.
Implementați oriunde și oriunde aveți nevoie pentru vizibilitate la fața locului, virtuală sau în cloud. NetProfiler este conceput pentru a răspunde nevoilor dvs. hibride și de cloud, fiind compatibil atât cu jurnalele de flux Azure NSG, cât și cu jurnalele de flux AWS VPC.
NetProfiler Advanced Security Module software opțional de analiză a securității. Acesta valorifică datele de flux pentru a detecta, investiga și atenua amenințările avansate. NetProfiler Advanced Security Module este deosebit de potrivit pentru vânătoarea de amenințări, răspunsul la incidente și analiza criminalistică a rețelelor.
Beneficiile cheie
Beneficiile monitorizării traficului de rețea

Monitorizare proactivă, nu reactivă
În prezent, performanța rețelei este indisolubil legată de performanța afacerii. Departamentul de operațiuni IT trebuie să înțeleagă modul în care performanța degradată și incidentele de securitate afectează utilizatorii finali și, în cele din urmă, afacerea. NetProfiler este un analizor NetFlow care utilizează analiza comportamentală pentru a stabili o linie de bază a comportamentelor normale ale rețelei, apoi alertează asupra schimbărilor care ar putea afecta experiența utilizatorilor sau indica o încălcare a securității.

Simplificați migrările
Migrarea aplicațiilor în cloud poate fi complexă și poate consuma mult timp. NetProfiler automatizează cartografierea tranzacțiilor aplicațiilor cu infrastructura lor de bază, astfel încât definițiile aplicațiilor și interdependențele lor să fie ușor de identificat și precise. Acest lucru simplifică o gamă întreagă de inițiative de schimbare IT, inclusiv migrațiile în cloud.

Planificați în mod corespunzător schimbările de capacitate
Este esențial să se asigure că rețelele dispun de resurse adecvate pentru a face față nevoilor actuale și viitoare de lățime de bandă. Cu ajutorul monitorizării traficului de rețea Alluvio NetProfiler, puteți obține informații despre capacitatea, utilizarea, performanța și compoziția traficului din rețea pentru a asigura livrarea de aplicații de înaltă performanță. Înțelegeți modul în care fluxurile de trafic din rețea se modifică în timp pentru a preveni surprizele nedorite care ar putea afecta utilizatorii.

Vizibilitate hibridă și multi-cloud
Obțineți aceeași monitorizare a traficului de rețea ușor de utilizat în mediile on-prem, virtuale și multi-cloud. Simplificați depanarea hibridă și reduceți punctele moarte ale rețelei și aplicațiilor cu până la 53%.
INTERFAȚA RIVERBED NETPROFILER


CYBERSECURITY
NetProfiler capturează date de rețea cu rezoluție completă – înregistrări de flux (NetFlow, sFlow, IPFIX etc.) și măsurători de performanță – în toate căile de rețea interne și în cloud
Folosește statisticile de bază și monitorizarea proactivă pentru a declanșa o alertă odată ce este detectată o abatere, fără a cunoaște în prealabil aplicațiile specifice, dependențele de traseu și numărul de utilizatori
Asigurați succesul mediului SD-WAN SteelConnect SD-WAN prin validarea politicilor care funcționează conform așteptărilor, rezolvarea rapidă a problemelor și o mai bună planificare.
• NetProfiler oferă trei moduri de a crea o definiție de aplicație personalizată. Puteți să faceți o hartă:
– Gazde, grupuri de gazde, protocoale, porturi la un nume de aplicație.
– Aplicații recunoscute automat la un nume de aplicație
– URL-uri la un nume de aplicație
• Inspecție profundă a pachetelor de trafic al aplicațiilor de la Riverbed® AppResponse, Riverbed® NetShark și SteelHead pentru o vizualizare și o analiză ușoară în tabloul de bord NetProfiler pentru a vă ajuta să distingeți rapid și precis aplicațiile critice pentru afaceri de cele recreaționale care rulează în întreaga rețea, inclusiv WAN-ul optimizat
• Include un asistent de descoperire care creează tablouri de bord ale aplicațiilor pentru a automatiza procesul de cartografiere a tranzacțiilor cu infrastructura lor de bază, astfel încât definițiile și interdependențele aplicațiilor să fie exacte – inclusiv descoperirea prin intermediul F5, Riverbed® SteelApp™ Traffic Manager și a altor controllere de livrare a aplicațiilor (ADC).
• Creează hărți de servicii pentru accelerarea depanării în ecosistemele de aplicații complexe și planificarea consolidării centrelor de date sau a inițiativelor de cloud, de recuperare în caz de dezastru și de virtualizare Analiza optimizării WAN
• Analiza robustă a mediilor optimizate Riverbed SteelHead și Interceptor vă permite să vă planificați cu ușurință implementările de optimizare, să evaluați impactul și să cuantificați beneficiile
• Depanarea rentabilă a problemelor din ramură folosind un singur produs pentru vizibilitate, control și optimizare
• Raportarea și monitorizarea centralizată a calității serviciului (QoS) de intrare și de ieșire din site și clase de calitate a serviciului (QoS)
• Monitorizarea bogată a peste 2000 de aplicații implicite și a aplicațiilor definite de către client
• Monitorizarea tuturor componentelor de rețea și de infrastructură implicate în furnizarea unui serviciu de aplicații, cum ar fi utilizatorii, serverele Web, balansoarele de sarcină, serverele de aplicații, serverele de autentificare și DNS, bazele de date și legăturile dintre acestea.
• Analiză avansată a modificărilor de performanță, oferind o notificare proactivă a problemelor de brewing
• Tablourile de bord ale serviciilor oferă o vizualizare rapidă a stării de sănătate de la un capăt la altul a unui serviciu de afaceri, care este prezentată vizual prin indicatori de stare de sănătate de culoare roșu-galben-verde
• O detaliere ghidată dezvăluie detalii despre cele mai critice aplicații an
Crearea de tablouri de bord cu un singur clic creează tablouri de bord centrate pe NetOps, specifice aplicațiilor, specifice optimizării SteelHead WAN și legate de VoIP, care evidențiază rapid datele relevante și eficientizează fluxurile de lucru pentru depanare.
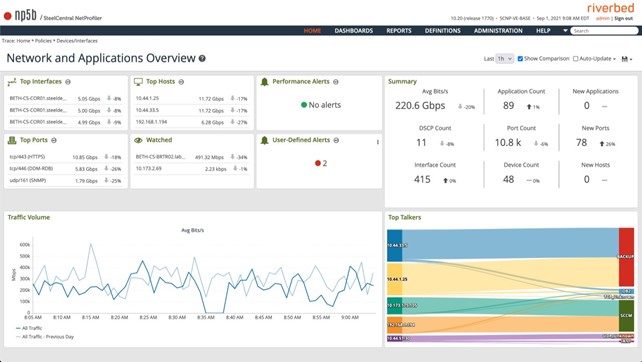
Oferă un rezumat instantaneu al principalilor indicatori cheie de performanță ai rețelei și aplicațiilor și modul în care aceștia s-au modificat; liste de alerte de performanță și de securitate recente; diagrama „Top Talkers sankey”; diagrame de trafic general; și o listă de supraveghere, astfel încât să puteți monitoriza ceea ce este important pentru dumneavoastră.
Formatul IPFIX compatibil cu NSX permite produselor Riverbed NPM să furnizeze informații detaliate despre ce rețele virtuale suprapuse NSX rulează pe rețeaua fizică, ce aplicații sunt implicate și ce gazde și puncte finale de tunel virtual generează traficul.
• NetProfiler poate fi implementat în
– AWS
– AWS GovCloud West
– Azure
– Azure Government (non-DoD, fără Iowa)
Următoarea telementrie de flux poate genera și trimite fluxuri pentru cloud către NetProfiler în cloud sau on-prem.
– AppResponse Cloud
– Jurnalele de flux AWS VPC
– Jurnalele de flux Azure NSG
– Vor funcționa și alte soluții externe/terestre care pot genera și trimite fluxuri în format standard (de exemplu, NFv5, v9, IPFIX etc.).
• Listele negre alertează cu privire la adrese IP cunoscute, CIDR-uri etc. care au fost identificate anterior ca fiind asociate cu activități rău intenționate.
• Fluxurile de amenințări sunt informații generate de analiști despre amenințări potențiale. Fluxurile de amenințări vă permit să citiți mai multe și să vă investigați rețeaua
• Detectați cu acuratețe atacurile DDoS volumetrice, de protocol și de tip aplicație în doar 10 secunde.
• Acționați imediat pentru a redirecționa chirurgical traficul către centrele de atenuare A10 TPS sau către centrele de curățare în cloud Verisign CloudSign
NetProfiler captează și stochează toate fluxurile, astfel încât aveți la dispoziție o analiză criminalistică de fidelitate completă pentru vânătoarea de amenințări. Faceți pivotare și detaliere pentru a urmări orice indiciu, iar datele vor fi întotdeauna acolo
Dispuneți de datele necesare pentru a vă recupera după un incident cibernetic cu rapiditate și precizie pentru a minimiza întreruperea activității
Analiză de securitate
Înțelegeți modelele schimbătoare de comportament din rețeaua dumneavoastră care indică amenințări la adresa securității:
- Conexiune suspectă: atunci când două gazde care nu comunică în mod normal încep să vorbească.
- Vierme: un model de scanare între gazde, în care sistemele scanate anterior devin brusc ele însele scanere. Se raportează identificarea pacientului zero, a gazdelor infectate și a mijloacelor de propagare
- Gazdă nouă: o gazdă care nu a fost identificată anterior a trimis suficient trafic pentru a fi considerată ca fiind intrată în rețea.
- Serviciu nou: o gazdă sau un grup automat de gazde furnizează sau utilizează un serviciu pe un port nou.
- Scanare gazdă: o serie de gazde sunt interogate pe același port.
- Scanare de port: o gazdă sau o serie de gazde este interogată pe o serie de porturi.
- Creștere bruscă a lățimii de bandă: o creștere semnificativă a traficului care corespunde caracteristicilor unui atac DoS sau DDoS.
Ai întrebări? Adresează-te unui expert Xontech Systems

