Backup și recuperare
APĂRAȚI-VĂ PENTRU VIITOR CU SECURITATEA INTELIGENTĂ A PUNCTELOR FINALE ȘI XDR INTEGRAT.
Pentru a depăși complexitatea crescândă a infrastructurilor IT și atacurile cibernetice sofisticate este nevoie de o soluție de backup cuprinzătoare pentru a păstra în siguranță fiecare bucată de date.
Acronis Cyber Protect integrează soluția de backup cu tehnologii avansate anti-ransomware pentru a vă proteja datele de orice amenințare.
Protejați datele în mediile fizice, virtuale, cloud și mobile.
Obțineți o recuperare rapidă și fiabilă a aplicațiilor, sistemelor și datelor dvs. pe orice dispozitiv, de la orice incident.
Apărați-vă datele cu protecția integrată împotriva ransomware-ului bazată pe MI și cu autentificarea blockchain.

Copie de rezervă a fișierelor și a imaginilor de disc
Efectuați copii de rezervă ale fișierelor individuale sau protejați-vă întreaga afacere prin copierea de rezervă a întregului sistem ca un singur fișier, asigurând o capacitate de restaurare de tip bare metal. În cazul unui dezastru de date, puteți restabili cu ușurință toate informațiile pe un hardware nou.
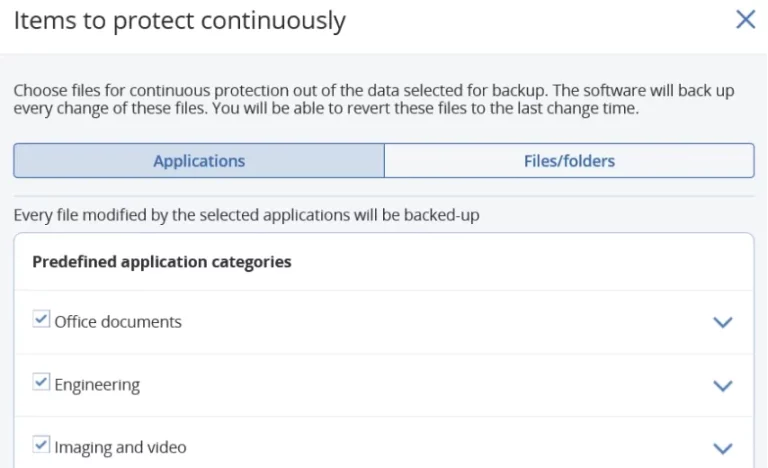
Protecția continuă a datelor
Asigurați-vă că utilizatorii nu-și pierd munca în curs de desfășurare prin definirea unei liste de aplicații esențiale care sunt utilizate frecvent. Agentul Acronis monitorizează fiecare modificare efectuată în aplicațiile din listă – indiferent unde salvează utilizatorul fișierul – și face în permanență copii de siguranță. Dacă sistemul trebuie să fie reimaginat, puteți restaura datele dintr-o copie de rezervă și aplica cele mai recente modificări, astfel încât să nu se piardă date.
Avantajele ACRONIS
Echilibrați valoarea datelor, infrastructura și orice cerințe de reglementare cu opțiuni de stocare flexibile. Creșteți cu ușurință folosind stocarea care se potrivește nevoilor dumneavoastră: NAS, SAN, benzi, discuri, Acronis Cloud sau orice cloud privat sau public, cum ar fi Azure, AWS sau Google.
Acronis stochează datele într-un format de backup unificat, astfel încât să puteți recupera cu ușurință pe orice platformă, indiferent de sistemul sursă. Reduceți riscurile și supraîncărcarea IT prin migrarea între diferite hipervizoare și către/de la mașini fizice (P2V, V2V, V2P și P2P) sau în cloud (P2C, V2C, C2C, C2V și C2P).
Reduceți la minimum timpii de nefuncționare costisitori prin restaurarea sistemelor Windows și Linux pe hardware diferit, inclusiv în medii fizice, virtuale sau de tip cloud. Depășind problemele de compatibilitate, tehnologia Acronis Universal Restore asigură o migrare rapidă și ușoară a sistemului cu câteva clicuri.
Reduceți timpii de recuperare cu cel mai bun RTO din industrie prin pornirea imediată a copiei de rezervă ca o mașină virtuală Windows sau Linux direct din spațiul de stocare. Aveți mașina virtuală funcțională în doar câteva secunde, în timp ce tehnologia Acronis Instant Restore vă mută datele în mod invizibil pe gazdă în fundal.
Protejați mai multe sisteme, reducând în același timp impactul asupra capacității de stocare a discurilor și a rețelei prin capturarea numai a blocurilor cu date care s-au modificat de la precedenta copie de rezervă. Dedublarea Acronis Cyber Backup minimizează spațiul de stocare prin detectarea repetițiilor de date și stocarea datelor identice o singură dată.
Fiecare sistem – fizic, virtual sau în cloud – și toate sarcinile de lucru sunt consolidate pentru a proteja datele pe toate platformele. Orice aplicație nouă este integrată fără probleme în mediul existent, oferind o protecție continuă și cuprinzătoare a datelor.
Evitați pierderile de date imprevizibile și îmbunătățiți în mod proactiv timpul de funcționare prin monitorizarea sănătății unităților. Prin utilizarea învățării automate pe baza rapoartelor S.M.A.R.T. și a diverșilor parametri ai sistemului de operare, Acronis Cyber Protect vă poate avertiza cu privire la o problemă a discului înainte ca aceasta să se producă. Acest lucru vă permite să luați măsurile de precauție necesare pentru a vă proteja datele.
Avantaj unic Acronis
Împiedicați restaurarea fișierelor infectate din copiile de rezervă cu ajutorul scanării malware integrate. Prin scanarea copiilor de rezervă complete de pe disc într-o locație centralizată, Acronis Cyber Protect poate ajuta la găsirea programelor malware – asigurând că utilizatorii restaurează o copie de rezervă curată, fără malware.
Avantaj unic Acronis
O imagine a sistemului de operare sau o aplicație dintr-o copie de rezervă infectată cu programe malware poate provoca o reinfectare continuă dacă este utilizată pentru recuperare fără a elimina programele malware. Eliminarea malware-ului detectat și aplicarea celor mai recente definiții anti-malware în timpul recuperării permite utilizatorilor să restaureze imaginea sistemului de operare în condiții de siguranță, reducând șansele de reinfectare.
Avantaj unic Acronis
Asigurați-vă că datele critice sunt protejate pentru raportarea conformității cu o hartă de protecție a datelor. Obțineți informații detaliate despre datele stocate și utilizați clasificarea automată a datelor pentru a urmări starea de protecție a fișierelor importante. Veți fi avertizat dacă fișierele sunt sau nu copiate de rezervă, ajutându-vă să vă protejați în continuare datele.
Avantaj unic Acronis
Listele de permisiuni tradiționale, globale, nu gestionează bine aplicațiile personalizate. Acronis Cyber Protect scanează copiile de rezervă cu ajutorul tehnologiilor anti-malware (MI, euristică comportamentală etc.) pentru a permite includerea în lista de aplicații unice din punct de vedere organizațional și pentru a evita viitoarele falsuri pozitive.
Avantaj unic Acronis
Maximizați utilizarea eficientă a unităților de bandă în timpul operațiunilor de backup și recuperare, permițând mai multor clienți să facă backup simultan pe o singură unitate de bandă. Utilizați această metodă atunci când o unitate de bandă este mai rapidă decât sursa de backup, deoarece permite unității de bandă să continue să se rotească, evitând întreruperile de scriere.
Utilizați toate dispozitivele de bandă disponibile pe sistem, permițând ca backup-ul unui singur client să se execute simultan pe mai multe unități de bandă. Utilizați această metodă atunci când aveți mai multe dispozitive de destinație și doriți ca o singură sarcină de backup să le utilizeze pe toate simultan în momentul backup-ului.
CYBERSECURITY
Anti-malware și antivirus
Protejați-vă în mod activ datele, aplicațiile și sistemele împotriva atacurilor avansate de astăzi. Cu Acronis Cyber Protect, obțineți funcționalități extinse ale Acronis Active Protection pentru a vă proteja datele în timp real cu ajutorul tehnologiilor antivirus, anti-malware, anti-ransomware, anti-ransomware și anti-cryptojacking heuristice statice și comportamentale bazate pe MI.

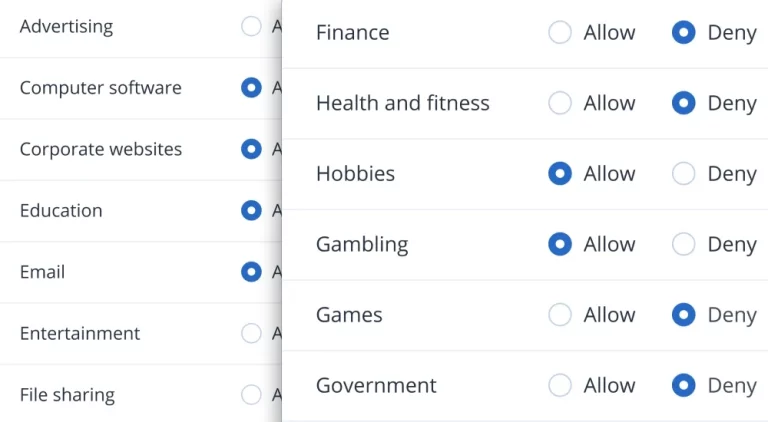
Filtrarea și clasificarea URL-urilor
Asigurați conformitatea și creșteți productivitatea prin prevenirea atacurilor din partea site-urilor web malițioase. Cu ajutorul filtrării avansate a URL-urilor, puteți controla accesul la site-urile web prin intermediul unui interceptor HTTP/HTTPS, al listelor de refuz și de autorizare pentru URL-uri și al analizei încărcăturii utile pentru URL-uri malițioase.
Protecție completă împotriva amenințărilor din zilele noastre
Avantaj unic Acronis
Centrele Acronis Cyber Protection Operation Centers (CPOC) monitorizează în permanență peisajul de securitate cibernetică și lansează alerte privind amenințările potențiale de orice fel. Primiți alerte în timp real cu privire la malware, vulnerabilități, dezastre naturale și alte evenimente globale care pot afecta protecția datelor, astfel încât să le puteți preveni.
Păstrați-vă datele mai sigure prin identificarea și remedierea vulnerabilităților din sistemul dumneavoastră. Cu evaluările noastre de vulnerabilitate, vă puteți scana mașinile pentru a vă asigura că toate aplicațiile și sistemele de operare sunt actualizate și nu pot fi exploatate de infractorii cibernetici.
Până la aplicarea unui patch, mașinile dumneavoastră sunt vulnerabile. Cu prevenirea exploatărilor, puteți opri și preveni atacurile cu ajutorul protecției memoriei, al protecției programării orientate spre revenire, al protecției prin injectare de cod și al protecției împotriva escaladării privilegiilor.
Instrumentele de colaborare precum WebEx și Zoom pot ajuta o organizație să devină mai eficientă, dar problema este că multe dintre aceste instrumente nu sunt sigure. Protejați în mod proactiv aceste instrumente de colaborare cu evaluări ale vulnerabilităților, gestionarea patch-urilor, prevenirea injectării de cod și capacități anti-malware.
RECUPERARE AVANSATĂ ÎN CAZ DE DEZASTRU
Recuperarea rapidă în urma atacurilor cibernetice și a altor întreruperi neplanificate
Acronis Advanced Disaster Recovery vă permite să restabiliți operațiunile în câteva clicuri, fără investiții inițiale, astfel încât să puteți recupera rapid sarcinile de lucru sau serviciile clienților în caz de ransomware, defecțiuni hardware și orice altă întrerupere.
Activați recuperarea în caz de dezastru cu câteva clicuri - fără a fi nevoie de investiții inițiale de capital.
Oferiți o protecție completă împotriva amenințărilor actuale - în timp ce vă creșteți veniturile lunare recurente.
Împiedicați reinfectarea prin trecerea la un punct de recuperare fără malware (disponibil cu Advanced Security).
Rămâneți în fața atacurilor cibernetice cu o soluție DRaaS completă
Puneți clienții în funcțiune în doar câteva minute prin pornirea sistemelor IT în Acronis Cloud cu conectivitate completă de la un site la altul și cu posibilitatea de a le recupera pe hardware similar sau diferit.

Recuperare rapidă
No matter the cause of the unplanned downtime, our disaster recovery technology ensures you achieve both RPOs and RTOs that are under 15 minutes. With the Acronis RunVM engine, you get near-instant production and test failover speeds, while flexible backup frequency policies can help you offer tighter RPOs.
Configurare în trei clicuri
Renunțați la hardware și la instalarea suplimentară și configurați-vă planul de recuperare în caz de dezastru în trei clicuri. Alegeți dintre mai multe șabloane cu diferite configurații de servere de recuperare, ceea ce vă permite să configurați rapid și ușor planurile de recuperare în caz de dezastru.


Gestionare ușoară
Nu este nevoie să adăugați, să învățați sau să gestionați o altă platformă. Configurați cu ușurință listele de servere, testați setările de conectivitate, configurați orchestrarea recuperării în caz de dezastru cu runbooks și recuperați pe mai multe rețele.
Furnizați cu ușurință servicii de recuperare în caz de dezastru
Orchestrarea recuperării în caz de dezastru
Simplificați recuperarea în caz de dezastru și creșteți eficiența operațională prin automatizarea failover-urilor și prin orchestrarea procedurilor de recuperare în caz de dezastru cu ajutorul runbook-urilor – un set de instrucțiuni care definesc modul în care trebuie să se rotească mediul de producție al clientului în cloud.

Minimizați timpul de nefuncționare, permițând recuperarea ușoară, scalabilă și eficientă, bazată pe cloud, a tuturor volumelor de lucru populare, inclusiv a serverelor fizice și a mașinilor virtuale Windows și Linux, a principalelor hipervizoare și a aplicațiilor Microsoft.
Asigurați un failover automat, rapid și ușor, al mediului de producție al clientului către un server extern care rulează în Acronis Disaster Recovery Storage sau către un hot storage din Acronis Cloud.
Activați conexiunea VPN securizată între site-ul local al clientului și site-ul cloud pentru a facilita comutarea parțială în caz de defecțiune a serverelor foarte dependente de pe site-ul local. Atunci când unul dintre servere este recreat pe site-ul cloud, serverele continuă să comunice, asigurând un timp de nefuncționare minim.
Efectuați teste de DR într-un mediu izolat pentru a confirma disponibilitatea aplicațiilor, pentru a asigura conformitatea și pentru a dovedi disponibilitatea DR – fără niciun impact asupra sistemelor de producție.
Obțineți vizibilitate în orchestrarea recuperării în caz de dezastru cu o vizualizare detaliată în timp real a execuției runbook-ului și a istoricului de execuție.
Prevent data loss and avoid data corruption with granularity of control over data protection and recovery capabilities. Restore systems and data to any recoverable point in the past, instead of to the latest one.
Consolidarea securității cu suportul IPSec multisite VPN care integrează protocoale și algoritmi securizați, astfel încât să puteți sprijini cu ușurință clienții cu mai multe site-uri care găzduiesc sarcini de lucru critice cu cerințe mai mari de securitate, conformitate și lățime de bandă.
Obțineți vizibilitate în orchestrarea recuperării în caz de dezastru cu o vizualizare detaliată în timp real a execuției runbook-ului și a istoricului de execuție.
Ai întrebări? Adresează-te unui expert Xontech Systems

