F‑Secure Elements
CLOUD PLATFORM FOR ALL YOUR BUSINESS SECURITY NEEDS.
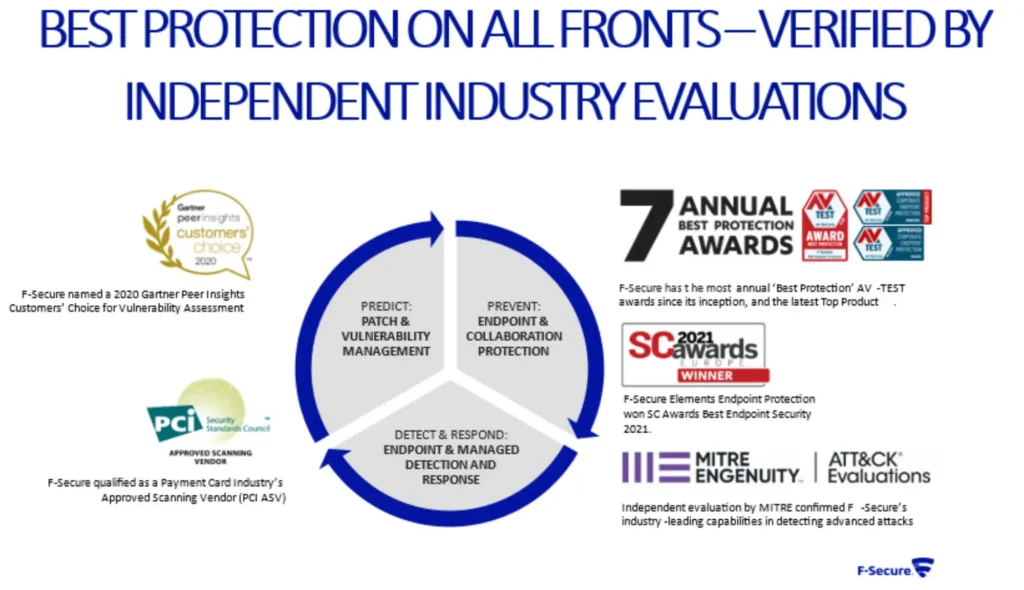
ALL-IN-ONE CYBERSECURITY PLATFORM
Manage all your security needs from a single console. F-Secure Elements gives you the clarity, flexibility and technology you need to adapt to changing threats and business needs.

All-In-One security solution
Unified endpoint protection across devices, clouds and servers.
F-Secure Elements solutions keep your business safe from modern cyber threats. Use individual solutions for specific needs or get complete protection by combining them all:
- F-Secure Elements Endpoint Protection for PCs, servers and mobile devices.
- F-Secure Elements Endpoint Detection and Response.
- F-Secure Elements Vulnerability Management.
- F-Secure Elements for Microsoft 365.
F-Secure Elements is a cloud-native platform that delivers everything from vulnerability management and collaboration protection to endpoint protection; and detection and response, the only four elements you need to cover the entire security value chain – all clearly visible and easy to manage from a single security console.
Supported systems
- Malware
- Ransomware
- Advanced Persistent Threats
- Zero Day Exploits
- Phishing Attempts
- Business Email Compromise (BEC)
- Brand and Domain Infringment
Discover the benefits of the elements
Elements put everything you need in one pane of glass, including asset prioritization, vulnerability identification, patch management, incident detection and more.
The elements gather and analyze all data from all solutions in real time, which means that when a problem is detected in one domain, responses are automatically triggered in all solutions.
Updates are handled automatically, without the need for additional server investments. This allows you to get the highest level of protection with the lowest upgrade costs.
With a flexible, usage-based SaaS option, Elements is very easy to manage internally. Or it can be purchased as a fully managed subscription service from one of our certified partners.

White Book
Quantify and communicate: cybersecurity ROI
Learn more about our cybersecurity ROI calculator, based on our extensive experience combined with solid statistical modeling, and apply it to your business case.
- Introduction to the concept of ROI in cyber security
- Explanation of ROI calculation methodology by F-Secure
- Concrete examples of ROI calculation
- Tips for communicating the ROI calculation to key stakeholders
- Guide to maximize your ROI
Got questions? Ask a Xontech Systems expert

