Backup and recovery
DEFEND FOR THE FUTURE WITH SMART ENDPOINT SECURITY AND INTEGRATED XDR.
Overcoming the growing complexity of IT infrastructures and sophisticated cyber attacks requires a comprehensive backup solution to keep every piece of data safe.
Acronis Cyber Protect integrates your backup solution with advanced anti-ransomware technologies to protect your data from any threat.
Protect data in physical, virtual, cloud and mobile environments.
Get fast and reliable recovery of your applications, systems and data on any device, from any incident.
Protect your data with built-in IM-based ransomware protection and blockchain authentication.

Backing up files and disk images
Back up individual files or protect your entire business by backing up your entire system as a single file, providing bare-metal restore capability. In the event of a data disaster, you can easily restore all your information to new hardware.
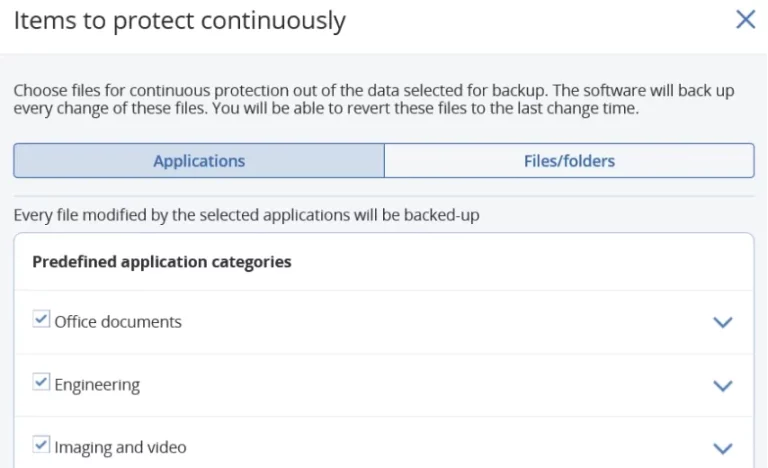
Continuous data protection
Ensure users don’t lose work in progress by defining a list of essential applications that are frequently used. Acronis Agent monitors every change made to the applications in the list – no matter where the user saves the file – and constantly backs up the file. If the system needs to be reimaged, you can restore data from a backup and apply the latest changes so that no data is lost.
Benefits of ACRONIS
Balance data value, infrastructure and any regulatory requirements with flexible storage options. Grow with ease using storage that fits your needs: NAS, SAN, tape, disk, Acronis Cloud, or any private or public cloud such as Azure, AWS or Google.
Acronis stochează datele într-un format de backup unificat, astfel încât să puteți recupera cu ușurință pe orice platformă, indiferent de sistemul sursă. Reduceți riscurile și supraîncărcarea IT prin migrarea între diferite hipervizoare și către/de la mașini fizice (P2V, V2V, V2P și P2P) sau în cloud (P2C, V2C, C2C, C2V și C2P).
Minimize costly downtime by restoring Windows and Linux systems to dissimilar hardware, including physical, virtual or cloud environments. Overcoming compatibility issues, Acronis Universal Restore technology makes system migration fast and easy with a few clicks.
Reduce recovery times with the industry’s best RTO by immediately booting your backup as a Windows or Linux virtual machine directly from storage. Have your virtual machine up and running in just seconds, while Acronis Instant Restore technology invisibly moves your data to the host in the background.
Protect multiple systems while reducing the impact on disk and network storage capacity by capturing only the data blocks that have changed since the previous backup. Acronis Cyber Backup deduplication minimizes storage space by detecting data repeats and storing identical data only once.
Every system – physical, virtual or in the cloud – and all workloads are consolidated to protect data across all platforms. Any new application is seamlessly integrated into the existing environment, providing continuous and comprehensive data protection.
Avoid unpredictable data loss and proactively improve uptime by monitoring drive health. By using machine learning based on S.M.A.R.T. reports and various operating system parameters, Acronis Cyber Protect can warn you of a disk problem before it occurs. This allows you to take the necessary precautions to protect your data.
Acronis Unique Advantage
Prevent infected files from being restored from backups with built-in malware scanning. By scanning full disk backups in a centralized location, Acronis Cyber Protect can help find malware – ensuring that users restore a clean, malware-free backup.
Acronis Unique Advantage
An operating system image or application from a backup infected with malware can cause continuous reinfection if used for recovery without removing the malware. Removing the detected malware and applying the latest anti-malware definitions during recovery allows users to safely restore the operating system image, reducing the chances of reinfection.
Acronis Unique Advantage
Ensure critical data is protected for compliance reporting with a data protection roadmap. Get detailed information about stored data and use automated data categorization to track the protection status of important files. You will be alerted whether or not files are backed up, helping you further protect your data.
Acronis Unique Advantage
Traditional, global permission lists do not handle customized applications well. Acronis Cyber Protect scans backups using anti-malware technologies (MI, behavioral heuristics, etc.) to enable inclusion in the organizationally unique application list and avoid future false positives.
Acronis Unique Advantage
Maximize the efficient use of tape drives during backup and recovery operations by allowing multiple clients to simultaneously back up to a single tape drive. Use this method when a tape drive is faster than the backup source because it allows the tape drive to keep spinning, avoiding write interruptions.
Use all available tape devices on the system, allowing a single client backup to run simultaneously on multiple tape drives. Use this method when you have multiple destination devices and want a single backup job to use all of them simultaneously at backup time.
CYBERSECURITY
Anti-malware and antivirus
Actively protect your data, applications and systems against today’s advanced attacks. With Acronis Cyber Protect, you get the extended capabilities of Acronis Active Protection to protect your data in real time with static and behavioral heuristic, IM-based antivirus, anti-malware, anti-ransomware, anti-ransomware, and anti-cryptojacking technologies.

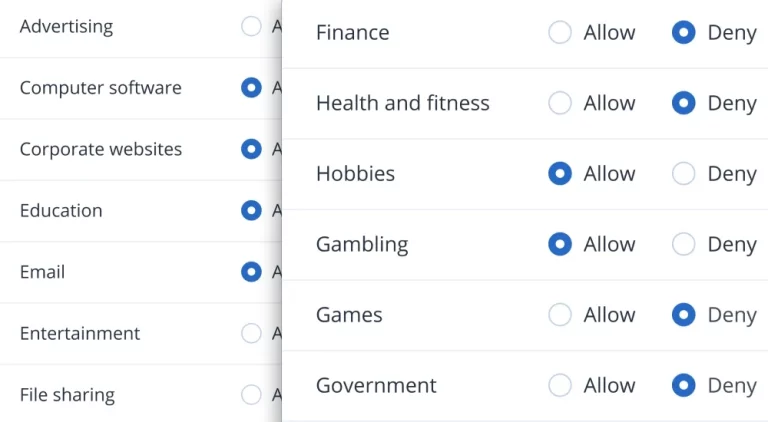
Filtering and categorizing URLs
Ensure compliance and increase productivity by preventing attacks from malicious websites. With advanced URL filtering, you can control access to websites with an HTTP/HTTPS interceptor, URL deny and allow lists, and payload analysis for malicious URLs.
Complete protection against today's threats
Acronis Unique Advantage
Acronis Cyber Protection Operation Centers (CPOCs) continuously monitor the cybersecurity landscape and issue alerts on potential threats of all kinds. Get real-time alerts on malware, vulnerabilities, natural disasters, and other global events that can affect data protection so you can prevent them.
Keep your data more secure by identifying and fixing vulnerabilities in your system. With our vulnerability assessments, you can scan your machines to ensure that all applications and operating systems are up-to-date and cannot be exploited by cybercriminals.
Until patched, your machines are vulnerable. With exploit prevention, you can stop and prevent attacks with memory protection, return-oriented scheduling protection, code injection protection, and privilege escalation protection.
Collaboration tools like WebEx and Zoom can help an organization become more efficient, but the problem is that many of these tools are not secure. Proactively protect these collaboration tools with vulnerability assessments, patch management, code injection prevention, and anti-malware capabilities.
ADVANCED DISASTER RECOVERY
Rapid recovery from cyber-attacks and other unplanned disruptions
Acronis Advanced Disaster Recovery lets you restore operations in a few clicks, with no upfront investment, so you can quickly recover your workloads or customer service in the event of ransomware, hardware failure, and any other disruption.
Activate disaster recovery with a few clicks - no upfront capital investment required.
Provide complete protection against today's threats - while increasing your recurring monthly revenue.
Prevent reinfection by switching to a malware-free recovery point (available with Advanced Security).
Stay ahead of cyber attacks with a complete DRaaS solution
Get customers up and running in minutes by powering up IT systems in the Acronis Cloud with full site-to-site connectivity and the ability to recover them to similar or different hardware.

Fast recovery
Indiferent de cauza întreruperii neplanificate a activității, tehnologia noastră de recuperare în caz de dezastru vă asigură atingerea unor RPO și RTO sub 15 minute. Cu motorul Acronis RunVM, obțineți viteze de failover aproape instantanee pentru producție și testare, în timp ce politicile flexibile privind frecvența backup-ului vă pot ajuta să oferiți RPO-uri mai stricte.
Three-click setup
Skip the additional hardware and installation and set up your disaster recovery plan in three clicks. Choose from multiple templates with different recovery server configurations, allowing you to quickly and easily set up your disaster recovery plans.


Easy management
No need to add, learn or manage another platform. Easily configure server lists, test connectivity settings, set up disaster recovery orchestration with runbooks, and recover across multiple networks.
Easily provide disaster recovery services
Orchestrating disaster recovery
Simplify disaster recovery and increase operational efficiencies by automating failovers and orchestrating disaster recovery procedures with runbooks – a set of instructions that define how to spin up your customer’s production environment in the cloud.

Minimize downtime by enabling easy, scalable, and efficient cloud-based recovery of all popular workloads, including physical servers and Windows and Linux virtual machines, leading hypervisors, and Microsoft applications.
Automatically, quickly and easily failover the client production environment to an external server running in Acronis Disaster Recovery Storage or to hot storage in Acronis Cloud.
Enable the secure VPN connection between the customer’s local site and the cloud site to facilitate partial failover in the event of a failure of the highly-dependent servers on the local site. When one of the servers is recreated on the cloud site, the servers continue to communicate, ensuring minimal downtime.
Perform DR testing in an isolated environment to confirm application availability, ensure compliance and prove DR availability – with no impact on production systems.
Gain visibility into disaster recovery orchestration with a detailed real-time view of runbook execution and execution history.
Preveniți pierderea de date și evitați coruperea datelor cu ajutorul controlului granular asupra capacităților de protecție și recuperare a datelor. Restaurați sistemele și datele la orice punct recuperabil din trecut, în loc de cel mai recent.
Enhance security with IPSec multisite VPN IPSec support that integrates secure protocols and algorithms so you can easily support customers with multiple sites that host critical workloads with higher security, compliance and bandwidth requirements.
Gain visibility into disaster recovery orchestration with a detailed real-time view of runbook execution and execution history.
Got questions? Ask a Xontech Systems expert

